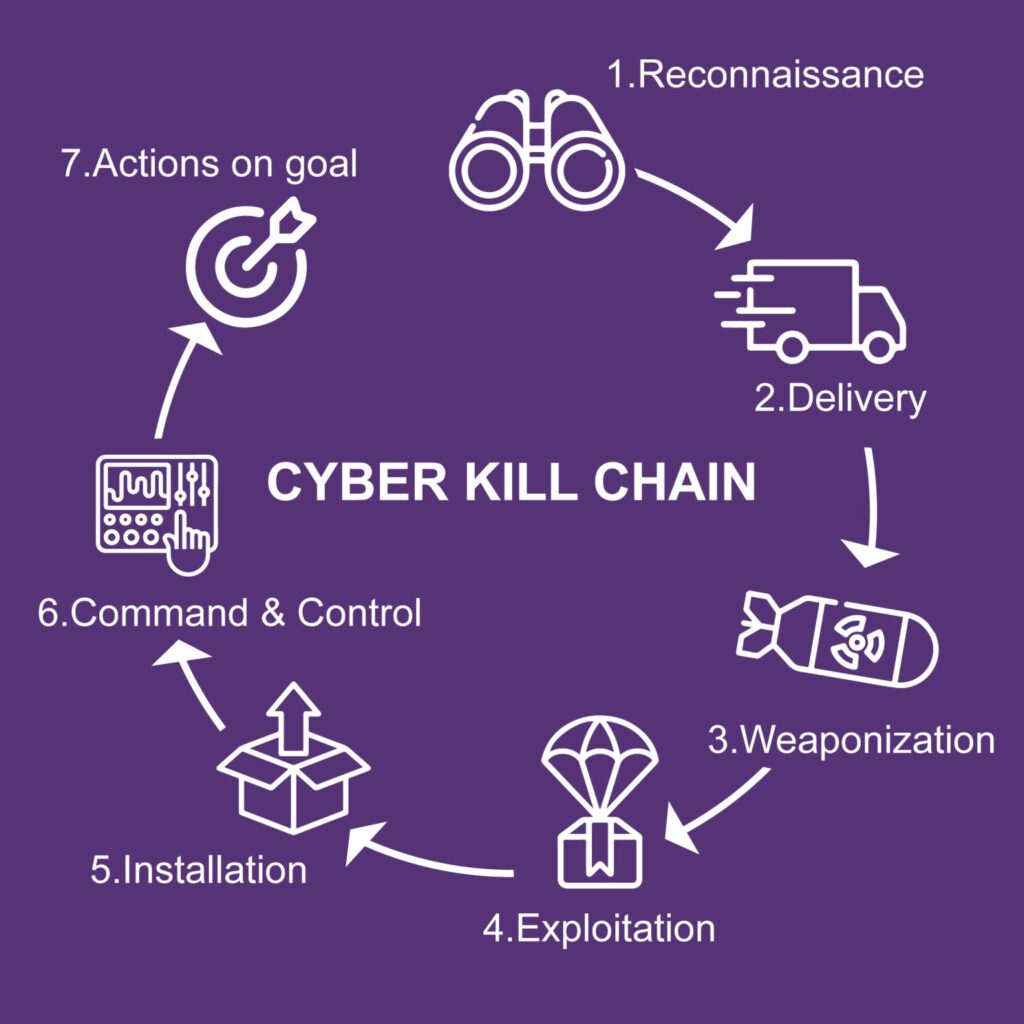
The Cyber Kill Chain framework came from Lockheed Martin to describe the stages that a cyber attack would normally flow through. Understanding this chain will help organizations and employees prepare ourselves across the trust gaps to proactive defense, improve incident response and conduct comprehensive risk assessments:
⚔ 1. Reconnaissance: Attackers gather information about the target, such as IP addresses, domain names, employee names, or email addresses. This stage helps them identify potential vulnerabilities or targets for further exploitation.
Example: attacker using publicly available information from social media profiles and company websites to identify employees and gather information about their roles and responsibilities.
⚔ 2. Weaponization: Attackers develop or obtain the tools and techniques required to exploit vulnerabilities. This stage involves creating malicious code, crafting spear-phishing emails, or acquiring exploit kits.
Example: attacker crafting a convincing email with a malicious attachment or link that, when opened, installs malware on the victim’s system.
⚔ 3. Delivery: Attackers deliver the weaponized payload to the target system. This can be done through various means, such as email attachments, malicious websites, or USB devices.
Example: a targeted phishing email containing a weaponized document that, when opened, triggers the execution of the malicious code.
⚔ 4. Exploitation: The weaponized payload is executed, taking advantage of vulnerabilities in the target system or application. Exploits could involve buffer overflows, code injection, or privilege escalation.
Example: an attacker exploiting a known vulnerability in a web server to gain unauthorized access and control over the system.
⚔ 5. Installation: Attackers install malware or backdoors onto the compromised system, allowing them to maintain persistence and control over the target environment.
Example: a remote access Trojan being installed on a compromised system, providing the attacker with remote access and control.
⚔6. Command and Control: Attackers establish a communication channel with the compromised system to remotely control and manage their malicious activities. This involves creating a backdoor or using existing protocols to maintain a covert channel of communication.
Example: an attacker using encrypted communication channels or legitimate protocols such as HTTP or DNS to communicate with the compromised system.
⚔ 7. Actions on goal: Finally, attackers achieve their primary objectives, which could include data exfiltration, unauthorized access, or disruption of services.
Example: an attacker stealing sensitive data, such as customer information or intellectual property, from the compromised system.
Leave a Reply