
Author: leduyduc
-
Cái ôm
Ngày tuyệt đẹp
Mưa mát cùng
Trái tim
Nhảy múa
Ngọt ngào
Có xíu lạc nhịp
Luống cuống
Thế nhưng trong sâu thẳm
Con tim rõ ràng
Yêu
Say khướt
Lâng lâng
-
Security Operations Center
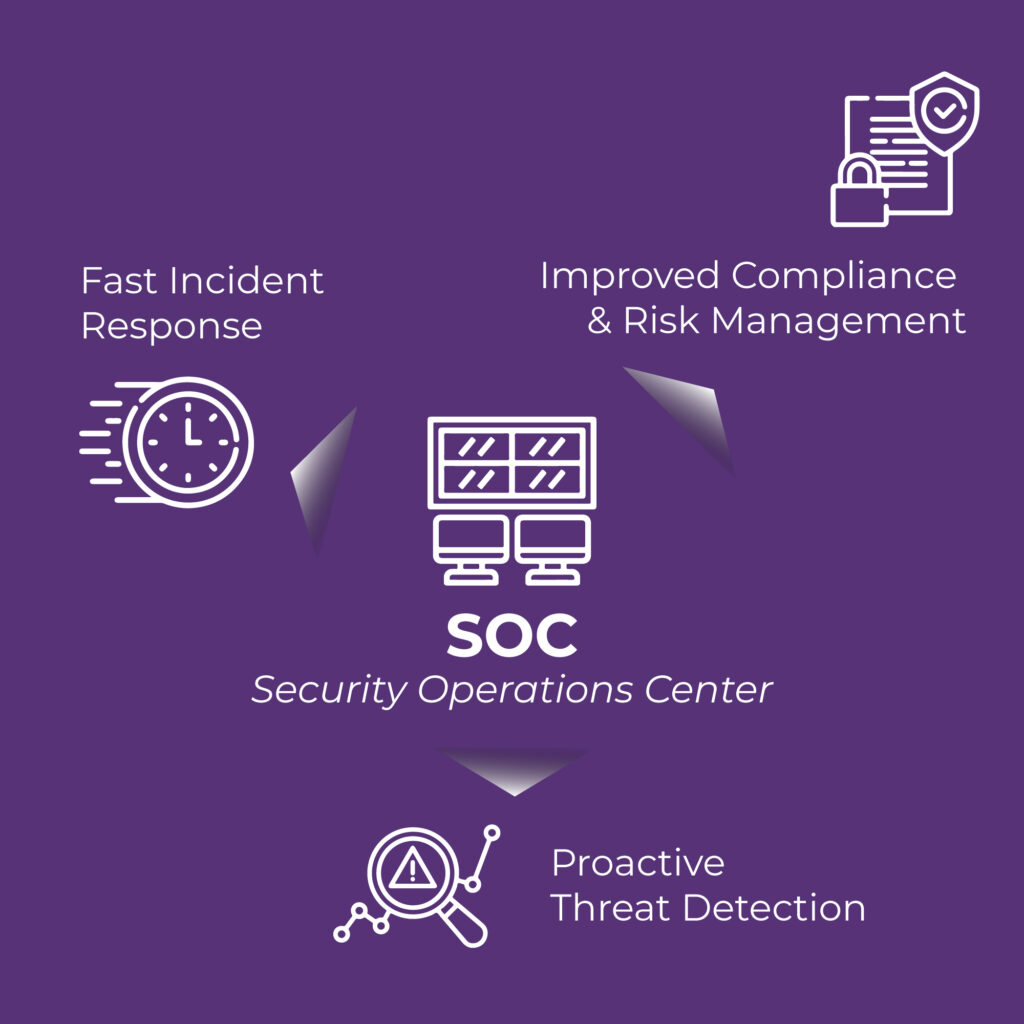
A Security Operations Center (SOC) is a centralized unit within an organization that is responsible for monitoring, detecting, and responding to cybersecurity threats and incidents. It is staffed by a team of security analysts who leverage advanced technologies, threat intelligence, and incident response processes to protect the enterprise’s networks, systems, and data.
The key benefits of a SOC for large enterprises are:
🕵♂️ Proactive Threat Detection: A SOC continuously monitors the enterprise’s network and systems, analyzing logs, events, and alerts to detect potential security threats and vulnerabilities. This proactive approach allows for early detection and response to security incidents, minimizing the impact of breaches and reducing potential financial and reputational damage. By staying ahead of emerging threats, the SOC can enhance the overall security posture of the enterprise.
⏱ Fast Incident Response: In the event of a security incident or breach, a SOC enables a swift and coordinated response. The security analysts in the SOC are trained to quickly assess the situation, contain the threat, investigate the incident, and mitigate any potential damage. This rapid incident response helps minimize downtime, limit data loss, and restore normal operations efficiently. Additionally, by documenting and analyzing incidents, the SOC can improve incident management processes over time.
📃 Improved Compliance and Risk Management: Large enterprises often need to comply with industry regulations and standards related to data protection and security. A SOC helps ensure compliance by monitoring security controls, generating audit logs, conducting risk assessments, and implementing necessary security measures. By actively managing risks and adhering to compliance requirements, the SOC helps the enterprise avoid penalties, legal issues, and reputational harm.
-
Zero Trust
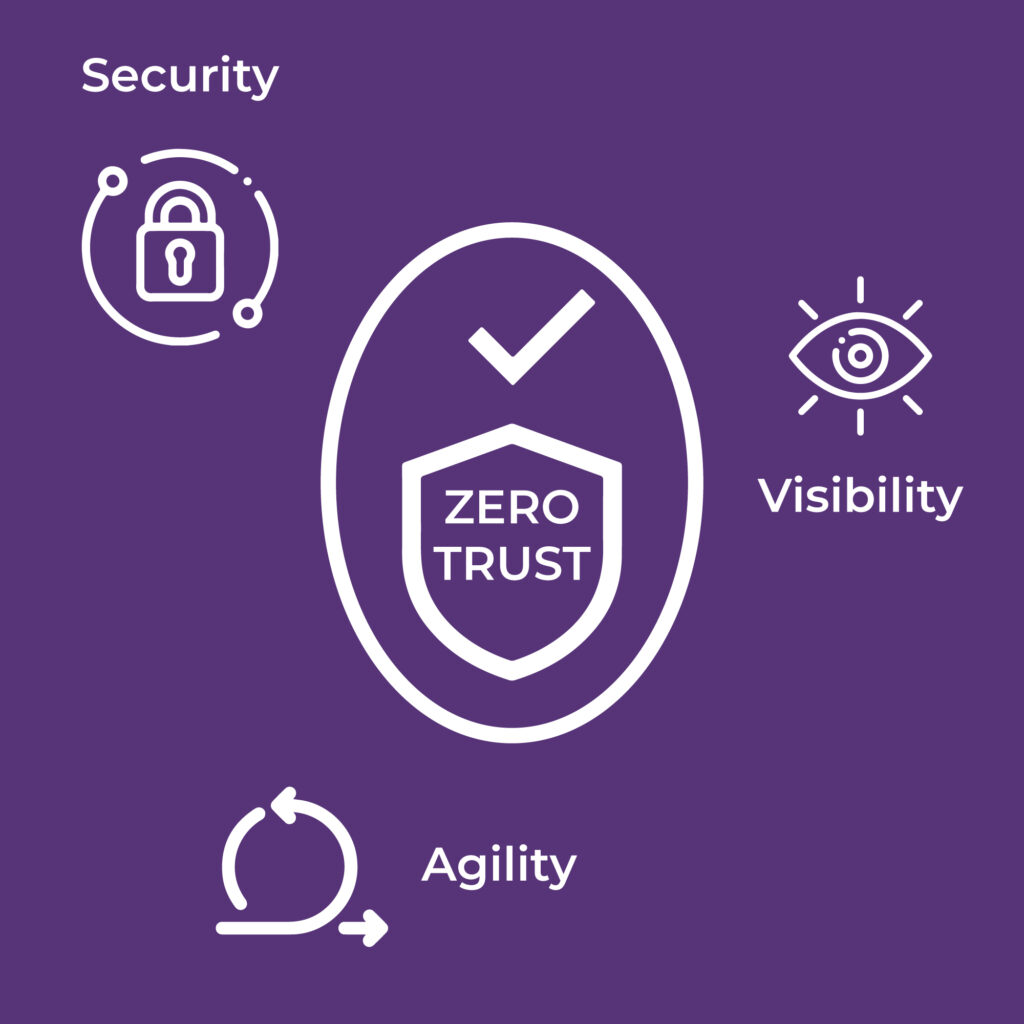
Zero Trust is a security framework that emphasizes strict access controls and continuous monitoring of network traffic, regardless of whether it originates from inside or outside the network perimeter. The primary benefit of implementing a Zero Trust architecture are:
🥇 Increased Security: Zero Trust architecture assumes that no user or device can be trusted by default and replaces the traditional perimeter-based security model with strict access controls and continuous monitoring. By implementing the principle of least privilege, Zero Trust limits user and device access to only the resources they need to perform their specific tasks. This significantly reduces the attack surface and minimizes the risk of unauthorized access, data breaches, and lateral movement within the network.
🥈 Improved Visibility: Zero Trust frameworks offer granular visibility into network activities and user behavior. By continuously monitoring traffic, organizations can detect anomalies, unusual behavior, and potential threats in real-time. This enables security teams to respond quickly and effectively to security incidents, mitigating potential damage. Zero Trust also emphasizes strong authentication and authorization mechanisms, ensuring that only authenticated and authorized users and devices can access sensitive resources.
🥉 Enhanced Agility: Zero Trust enables organizations to embrace modern business requirements such as remote work, mobile devices, and cloud-based applications without sacrificing security. By adopting Zero Trust principles, organizations can provide secure access to resources from any location, device, or network. This flexibility enhances productivity and enables businesses to adapt to changing work environments seamlessly. Zero Trust also supports the adoption of cloud services and third-party integrations, as access controls are enforced regardless of the location or origin of network traffic.
-
Pyramid of Pain
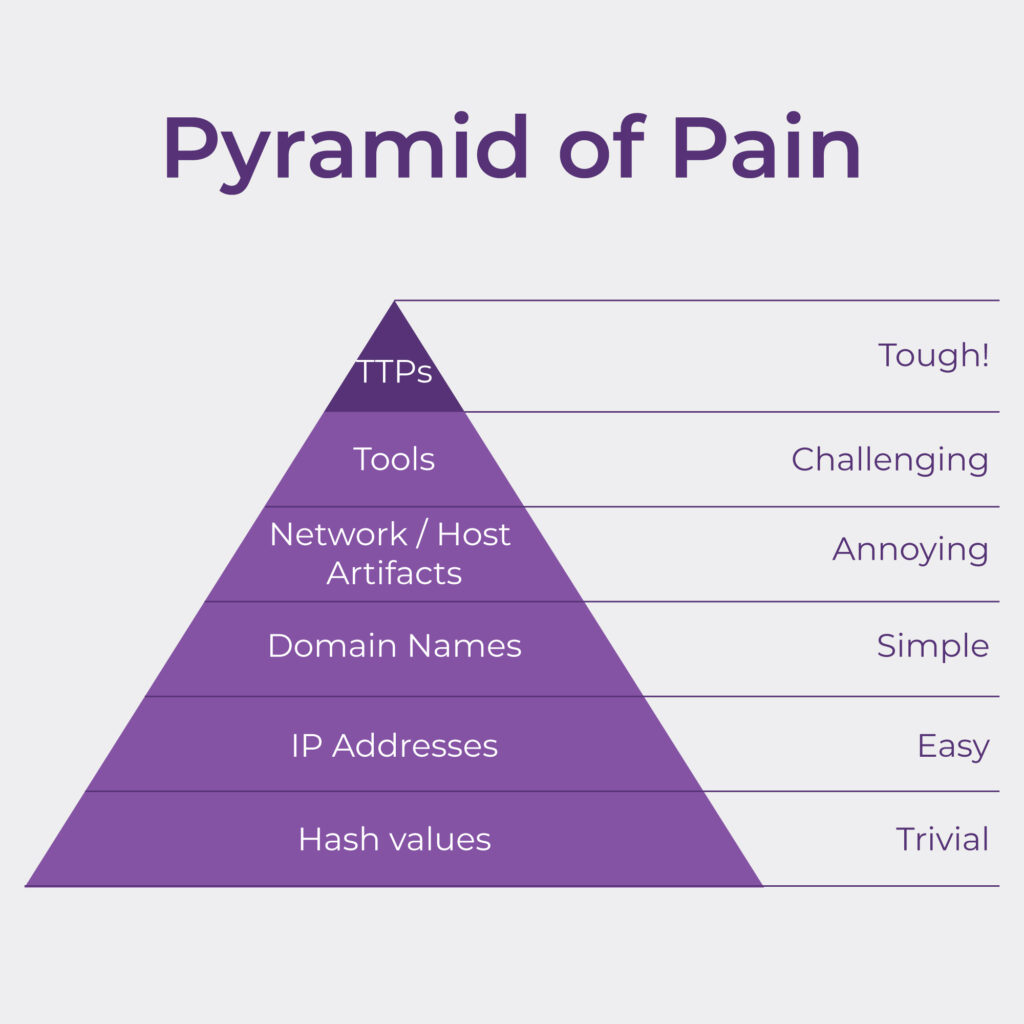
Pyramid of Pain is a cybersecurity concept to illustrate the hierarchy of indicators of compromise (IOCs) based on their level of difficulty and effectiveness for an attacker. The concept was introduced by cybersecurity expert David J. Bianco.
Pyramid of Pain holds significance for both cybersecurity specialists and business leaders in these ways:
1️⃣ Prioritization of defense measures: this helps specialists focusing on the indicators that are more difficult for attackers to change or modify, thereby making it harder for attackers to operate within their systems and detect and respond to threats more effectively.
2️⃣ Enhanced detection and response: cybersecurity specialists build more robust detection and response strategies by zeroing in on higher-level indicators. They can develop more sophisticated algorithms, security controls, and monitoring systems to identify and mitigate threats.
3️⃣ Strategic decision making: Pyramid of Pain offers business leaders insights into the motivations, goals, and strategies of attackers. This knowledge can inform strategic decision making, such as resource allocation, investments in security technologies, and the development of proactive security measures.
4️⃣ Risk management and compliance: The Pyramid of Pain helps in identifying and managing cybersecurity risks. By understanding the significance of different indicators, specialists can focus on mitigating the risks associated with higher-level indicators that are more difficult for attackers to modify. Furthermore, the concept aligns with various cybersecurity frameworks and compliance requirements, assisting enterprises in meeting regulatory standards.
Reference:
Bianco, D. J. (2014, January 17). The Pyramid of Pain. Enterprise Detection & Response. https://detect-respond.blogspot.com/2013/03/the-pyramid-of-pain.html
-
If I Ain’t Got You
Some people live for the fortune
Some people live just for the fame
Some people live for the power, yeah
Some people live just to play the game
Có người sống vì tiền tài
Có người sống chỉ vì danh vọng
Có người sống vì quyền lực
Rồi người sống với trò chơi cuộc đờiSome people think
That the physical things
Define what’s within
And I’ve been there before
That life’s a bore
So full of the superficial
Có người nghĩ rằng
Khoác những thứ phù hoa vật chất
Sẽ định giá cho chính con người họ
Và anh đã từng nghĩ như thế đó
Ôi cuộc đời buồn chán làm sao
Đầy rẫy những điều rỗng tuếchSome people want it all
But I don’t want nothing at all
If it ain’t you, baby
If I ain’t got you, baby
Vậy mà người ta muốn hết những thứ ấy
Nhưng anh sẽ chẳng muốn một thứ gì trên cuộc đời này cả
Nếu cuộc đời không có một thứ, đó là em, em ơi
Nếu cuộc đời của anh không có một thứ, đó là em, em yêu ơiSome people want diamond rings
Some just want everything
But everything means nothing
If I ain’t got you, yeah
Có người muốn những chiếc nhẫn kim cương lấp lánh
Có người muốn tất tần tật những thứ xa hoa
Nhưng tất cả sẽ là không là gì cả
Nếu anh chẳng có em, em ơiSome people search for a fountain
Promises forever young
Some people need three dozen roses
And that’s the only way to prove you love them
Có người mải mê tìm một hồ nước thần tiên
Để nguyện ước mãi trẻ chẳng già
Có người muốn chùm hoa hồng đỏ
Để là cách duy nhất chứng tỏ mình đang yêu họ thật đóHand me the world
On a silver platter
And what good would it be?
With no one to share
With no one who truly cares for me?
Nếu trong tay anh có vạn vật của thế gian
Trưng bày lên một đĩa bạc quý giá
Liệu anh có hạnh phúc đủ đầy?
Nếu chẳng có ai cùng chung vui
Và chẳng có người thương quan tâm ở bên cạnh?Some people want it all
But I don’t want nothing at all
If it ain’t you, baby
If I ain’t got you, baby
Ấy vậy mà người ta vẫn muốn có vạn vật của thế gian
Mà em ơi, anh sẽ chẳng muốn một thứ gì trên cuộc đời này cả
Nếu cuộc đời không có một thứ, đó là em, chỉ cần em thôi
Nếu cuộc đời của anh không có một thứ, đó là em, em yêu ơiSome people want diamond rings
Some just want everything
But everything means nothing
If I ain’t got you
Có người muốn những chiếc nhẫn kim cương chói sáng
Có người muốn mọi vật trên đời
Nhưng vạn vật sẽ là chả ý nghĩa gì cả
Nếu anh không có em, không có emSaid nothing in this whole wide world don’t mean a thing
If I ain’t got you with me, baby
Thế gian rộng lớn thế mà trống rỗng vô vị cả
Nếu anh không có em, em yêu ơi
-
A thousand years
Heart beats fast, colors and promises
Tim anh loạn nhịp muốn lạc quên những hẹn thề và hạnh phúc rực rỡHow to be brave, how can I love when I’m afraid to fall?
Làm sao để mạnh mẽ, làm sao để yêu khi nỗi sợ thất bại bao trùm lấy anh đây?But watching you stand alone
Nhưng khi thấy em cô độc một mìnhAll of my doubt suddenly goes away somehow
Chẳng hiểu sao mọi ưu tư trong anh tan biếnOne step closer
Một bước nữa thôi anh ở gần em hơnI have died every day waiting for you
Darling, don’t be afraid, I have loved you
For a thousand years
I’ll love you for a thousand more
Anh đã chết mỗi ngày trong chờ đợi
Thế nên em yêu ơi, đừng sợ nhé, anh vẫn luôn yêu em
Một ngàn năm rồi
Và vẫn như thế một ngàn năm nữaTime stands still, beauty in all she is
Vẻ đẹp em khiến thời gian như chết lặngI will be brave, I will not let anything take away
Và anh tràn đầy dũng khí để bảo vệWhat’s standing in front of me
Người con gái tuyệt trần trước mắt anhEvery breath, every hour has come to this
Từng hơi thở, từng phút giây đã dành tặng anhOne step closer
Một bước nữa thôi anh ở gần em hơnI have died every day waiting for you
Darling, don’t be afraid
I have loved you for a thousand years
I’ll love you for a thousand more
Anh đã chết mỗi ngày trong chờ đợi
Thế nên em yêu ơi, đừng sợ nhé, anh vẫn luôn yêu em
Một ngàn năm rồi
Và vẫn như thế một ngàn năm nữaAnd all along I believed I would find you
Time has brought your heart to me
I have loved you for a thousand years
I’ll love you for a thousand more
Anh luôn tin anh sẽ tìm thấy em
Dù gì đi nữa thời gian sẽ tác nguyện trái tim em dành cho anh
Anh đã yêu em một ngàn năm rồi
Và anh sẽ vẫn yêu em một ngàn năm nữaOne step closer
Một bước nữa thôi anh ở gần em hơn
One step closer
Một bước nữa thôi anh ở gần em hơn
-
Promise me
You light up another cigarette
And I pour the wine
Anh suy tư khói thuốc
Em rót đầy rượu vang
It’s four o’clock in the morning
And it’s starting to get light
Trời đã bốn giờ sáng
Và ngày dần tỏ rạng
Now I’m right where I want to be
Losing track of time
But I wish that it was still last night
Em đến nơi cần đến
Đầu trống rỗng thời gian
Tối qua qua rồi sao?
You look like you’re in another world
But I can read your mind
How can you be so far away lying by my side?
Anh như người xa lạ
Em hiểu anh, anh à
Nhưng tại sao anh lại
Người gần mà lòng xa
When I go away I’ll miss you
And I will be thinking of you
Every night and day just
Dù ở xa, em nhớ
Và sẽ nghĩ về anh
Mỗi đêm và mỗi ngày
Vì vậy…Promise me you’ll wait for me
‘Cause I’ll be saving all my love for you
And I will be home soon
Hứa với em, anh nhé
Anh sẽ đợi em về
Vì tình yêu em đó
Dành trọn cho anh rồi
Em về sớm, anh nhaPromise me you’ll wait for me
I need to know you feel the same way, too
And I’ll be home, I’ll be home soon
Hứa với em đi mà
Anh sẽ đợi em về
Em muốn biết anh ơi
Liệu anh cũng mong vậy?
Em hứa, em sẽ về
Về nhà sớm với anh
-
Advanced Persistent Threats (APTs)

APTs are sophisticated and targeted cyber attacks conducted by skilled and persistent threat actors.
APTs pose significant danger to organizations’ cybersecurity defenses due to their complexity, duration, and objectives.
⌨ APTs often leverage multiple advanced attack vectors (zero-day exploits, custom malware, social engineering, spear-phishing, and other stealthy tactics) to achieve their objectives.
⌛ APTs are designed to establish a long-term presence within the targeted network or system.
🥅 APTs focus on specific organizations or individuals of interest, such as government agencies, defense contractors, financial institutions, or organizations with valuable intellectual property. APTs are primarily motivated by espionage, data theft, intellectual property theft, sabotage, or disruption of critical systems.
⚔ APT attacks involve a well-organized and coordinated effort by skilled threat actors. They carefully plan their operations, continuously adapt their tactics, techniques, and procedures (TTPs) to evade detection, and persistently pursue their objectives.
📂 A key aspect of APTs is the covert extraction of sensitive data from the targeted organization. APTs focus on exfiltrating data without raising alarms, often using encrypted channels, steganography, or other concealment techniques to hide their activities.
🗺 APTs are often associated with nation-states or state-sponsored groups. These entities possess significant resources, advanced capabilities, and strategic motivations to conduct persistent and sophisticated cyber operations.
Notable APT campaigns are:
💼 Stuxnet: Stuxnet was a highly sophisticated APT attributed to a joint effort by the United States and Israel in 2010. It targeted Iran’s nuclear facilities, specifically its uranium enrichment centrifuges, by exploiting zero-day vulnerabilities in Windows. Stuxnet caused physical damage to Iran’s nuclear program.
💼Operation Aurora: Occurring in 2009, Operation Aurora was a series of APT attacks that targeted major technology companies, including Google, Adobe, and Juniper Networks. The attackers used spear-phishing emails to gain initial access and exploited zero-day vulnerabilities in popular software applications. The goal of the campaign was to steal intellectual property and gain unauthorized access to email accounts.
💼Carbanak: Carbanak, also known as Anunak, is an APT group that targeted financial institutions worldwide. Active from 2013 to 2016, the group used spear-phishing emails and sophisticated malware to compromise banks’ networks. Carbanak stole hundreds of millions of dollars by manipulating ATM systems, conducting fraudulent transfers, and exploiting banking systems’ weaknesses.
-
Cyber Kill Chain
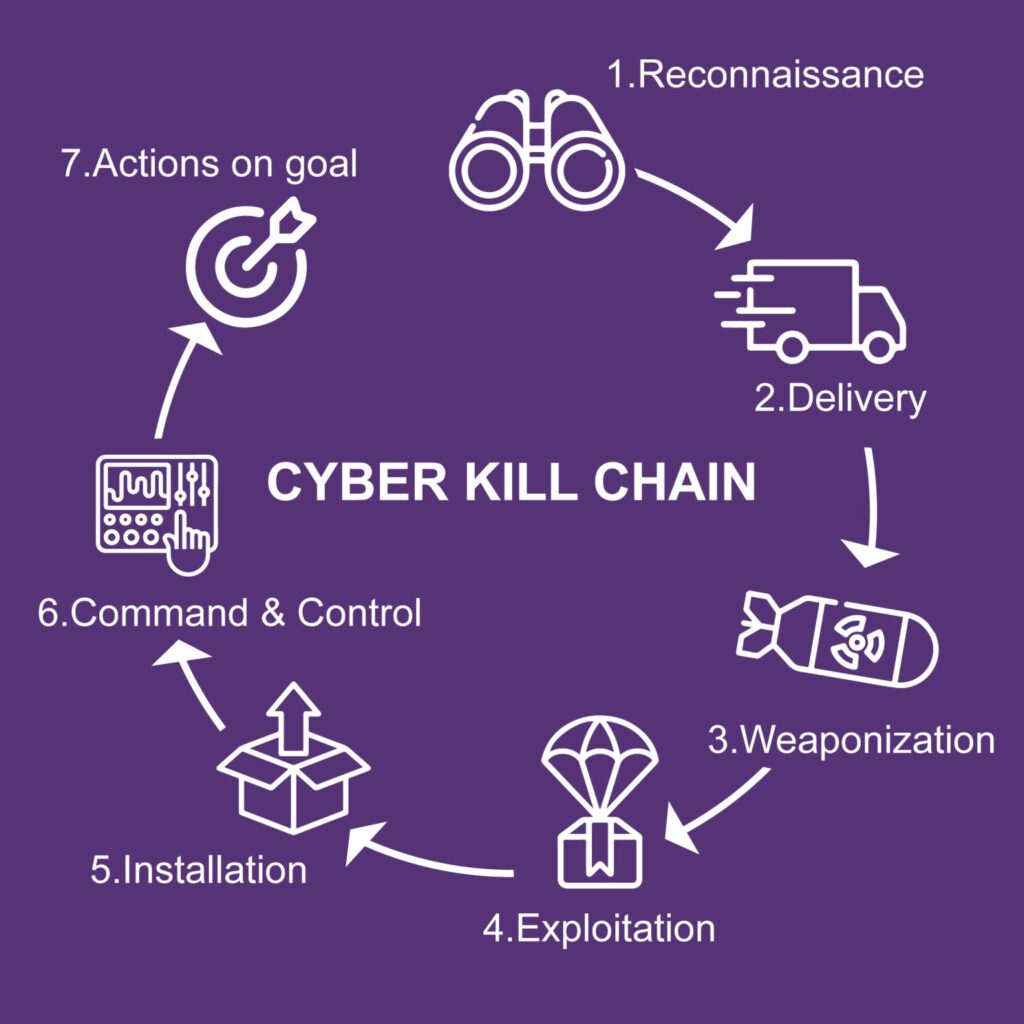
The Cyber Kill Chain framework came from Lockheed Martin to describe the stages that a cyber attack would normally flow through. Understanding this chain will help organizations and employees prepare ourselves across the trust gaps to proactive defense, improve incident response and conduct comprehensive risk assessments:
⚔ 1. Reconnaissance: Attackers gather information about the target, such as IP addresses, domain names, employee names, or email addresses. This stage helps them identify potential vulnerabilities or targets for further exploitation.
Example: attacker using publicly available information from social media profiles and company websites to identify employees and gather information about their roles and responsibilities.⚔ 2. Weaponization: Attackers develop or obtain the tools and techniques required to exploit vulnerabilities. This stage involves creating malicious code, crafting spear-phishing emails, or acquiring exploit kits.
Example: attacker crafting a convincing email with a malicious attachment or link that, when opened, installs malware on the victim’s system.⚔ 3. Delivery: Attackers deliver the weaponized payload to the target system. This can be done through various means, such as email attachments, malicious websites, or USB devices.
Example: a targeted phishing email containing a weaponized document that, when opened, triggers the execution of the malicious code.⚔ 4. Exploitation: The weaponized payload is executed, taking advantage of vulnerabilities in the target system or application. Exploits could involve buffer overflows, code injection, or privilege escalation.
Example: an attacker exploiting a known vulnerability in a web server to gain unauthorized access and control over the system.⚔ 5. Installation: Attackers install malware or backdoors onto the compromised system, allowing them to maintain persistence and control over the target environment.
Example: a remote access Trojan being installed on a compromised system, providing the attacker with remote access and control.⚔6. Command and Control: Attackers establish a communication channel with the compromised system to remotely control and manage their malicious activities. This involves creating a backdoor or using existing protocols to maintain a covert channel of communication.
Example: an attacker using encrypted communication channels or legitimate protocols such as HTTP or DNS to communicate with the compromised system.⚔ 7. Actions on goal: Finally, attackers achieve their primary objectives, which could include data exfiltration, unauthorized access, or disruption of services.
Example: an attacker stealing sensitive data, such as customer information or intellectual property, from the compromised system.